When you create an AWS account, a root user is created using the email address and password provided during the account creation process. This user has unlimited access to all resources and services in the account. Therefore, it is essential to protect this user and discourage its use for daily operations. In reality, the root user is only required in very specific situations.
How root account works in an AWS Organization#
When we create an AWS account under an AWS Organization, the process is slightly different. We provide an email address that serves as the identifier for the AWS account root user, but we do not set a password. Behind the scenes, AWS generates a random password. If we later need to access the organization’s account as the root user, we can simply request a password recovery through the login console.
IAM Root Access Management#
IAM Root Access Management is a new AWS IAM capability that allows centralized management of root credentials (enabling or disabling them), blocking the password recovery process, and performing privileged root actions in member accounts.
Privileged root actions in member accounts#
With this feature, it is possible to perform certain root actions in member accounts, such as deleting misconfigured resource policies in Amazon SQS or Amazon S3.
As of the time of writing this post, the allowed privileged actions are:
- Deleting an S3 bucket policy
- Deleting an SQS queue policy
Root credentials management#
This feature allows you to delete and audit the root credentials of member accounts. Additionally, it enables password recovery for specific member accounts.
The AWS Console only allows these actions to be performed on a per-account basis, meaning it is not possible to delete root credentials across multiple accounts simultaneously. To achieve root credential deletion for several accounts at once, this must be done programmatically.
Setup and basic usage from the AWS console#
Before using Root Access Management, it must first be enabled. Let’s go through the steps to enable Root Access Management and use it from the AWS Console.
In the AWS IAM Console, enable Root Access Management on the Account settings page.
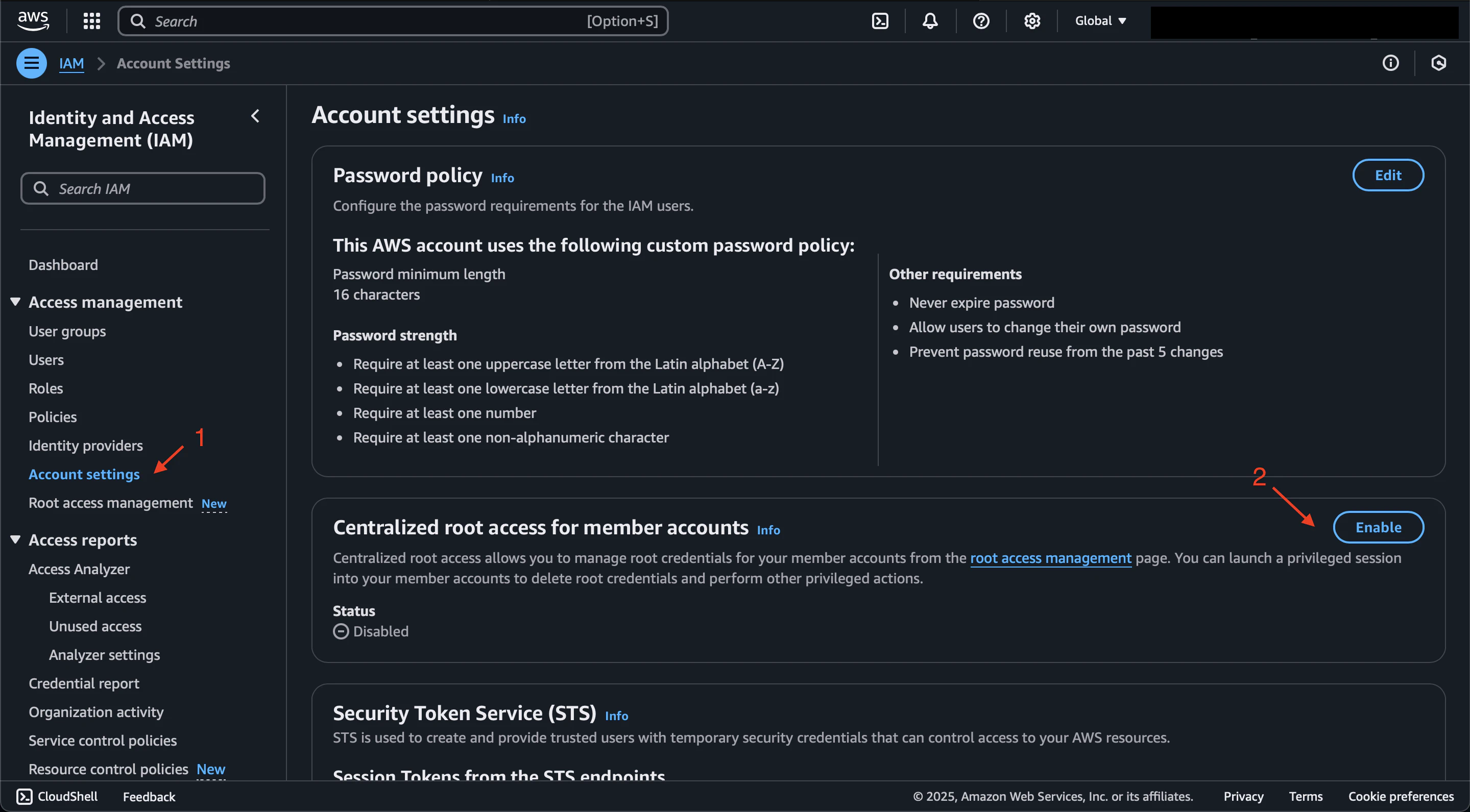
Select the capabilities to enable. For this demo, we will leave the default options selected.
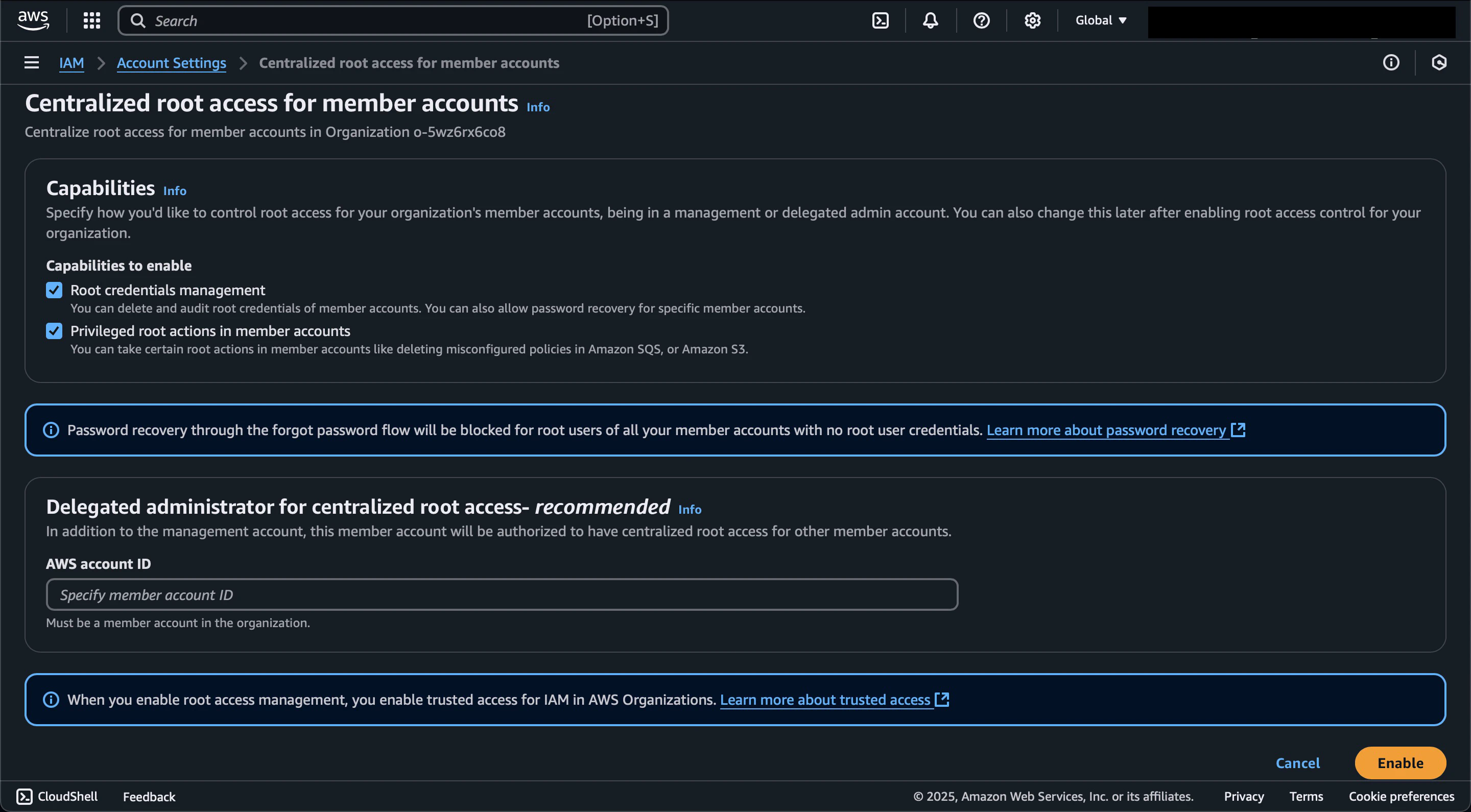
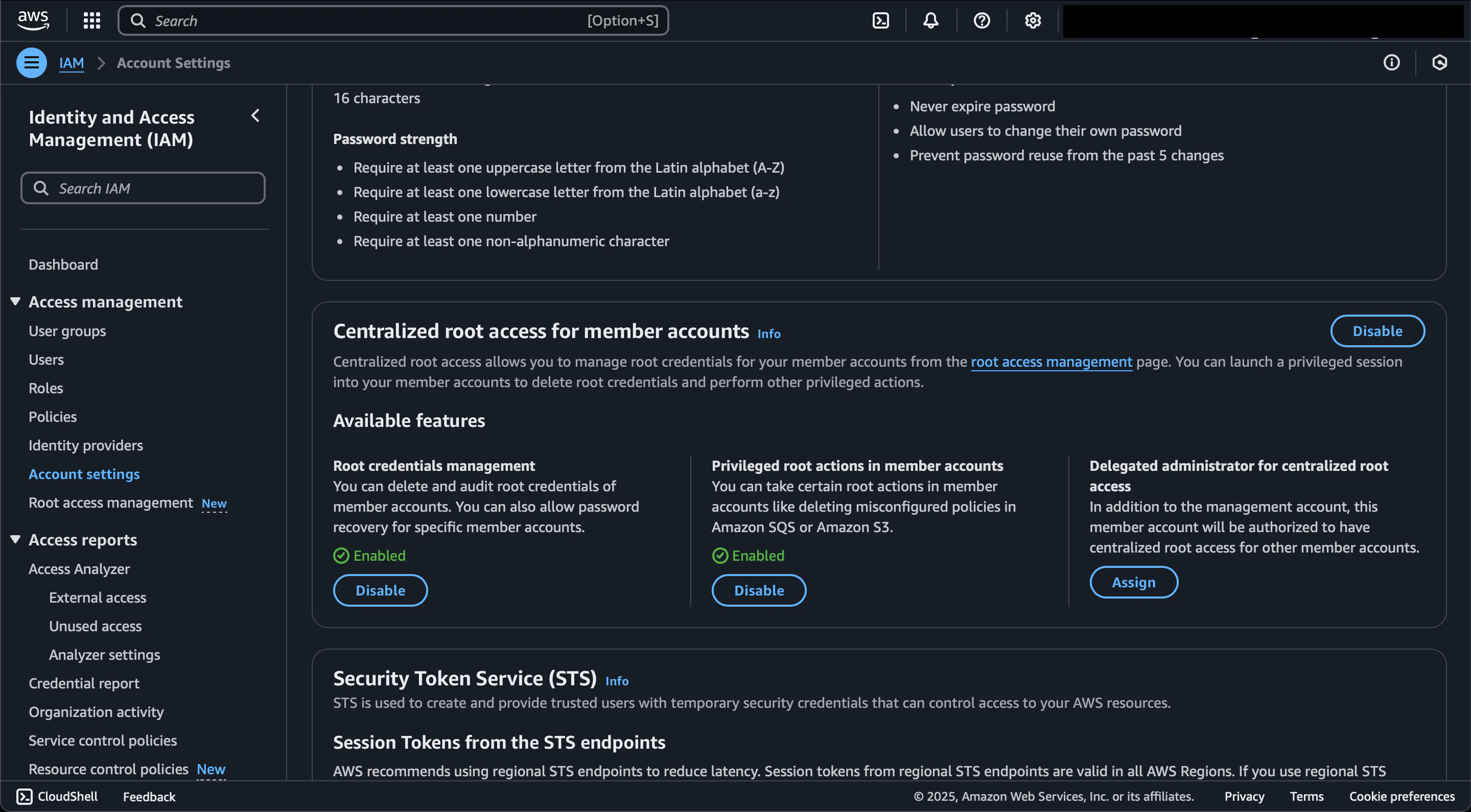
On the Account settings page, we can review our configuration.
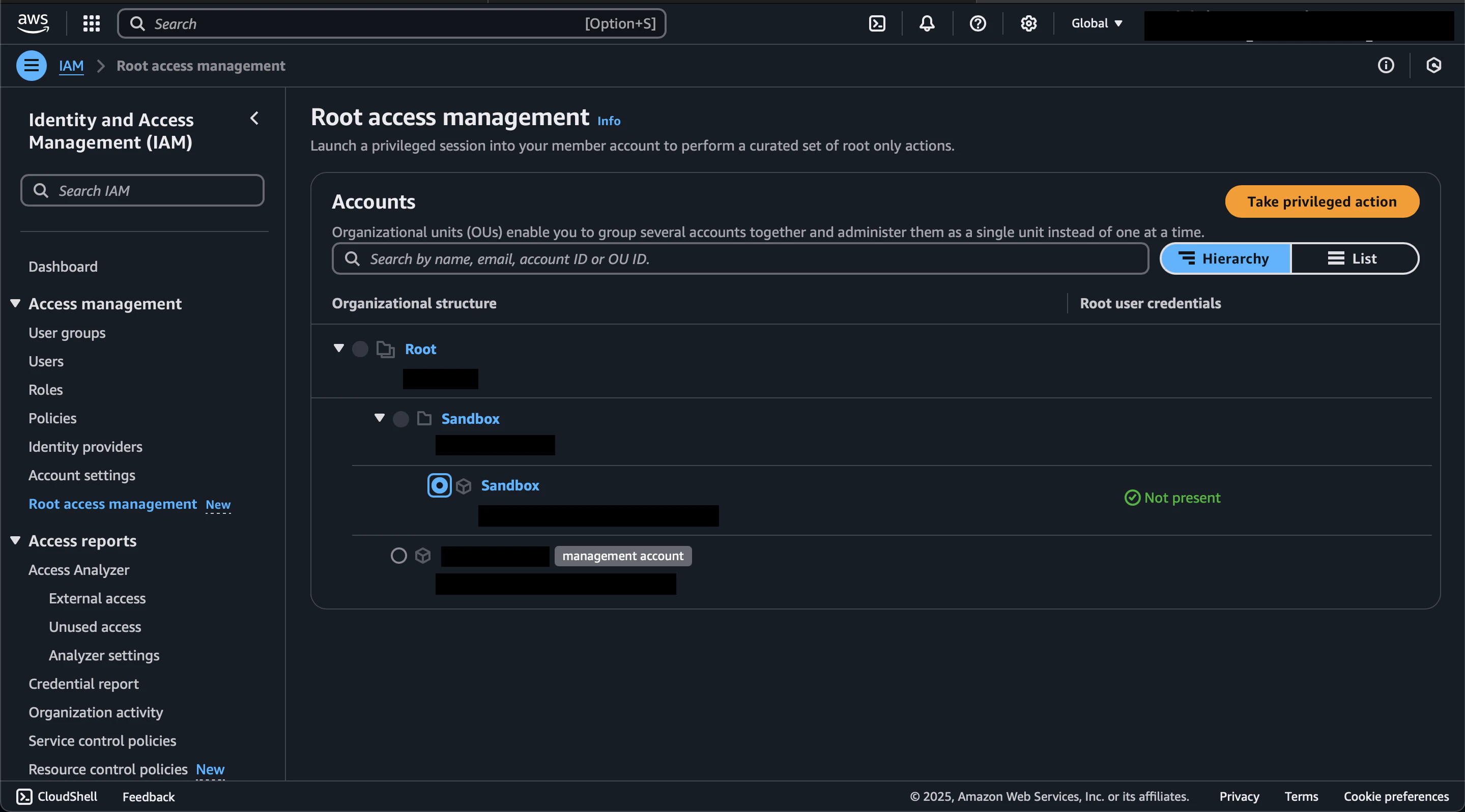
On the Root Access Management page, we can see that the root user in the Sandbox account has the console password enabled.
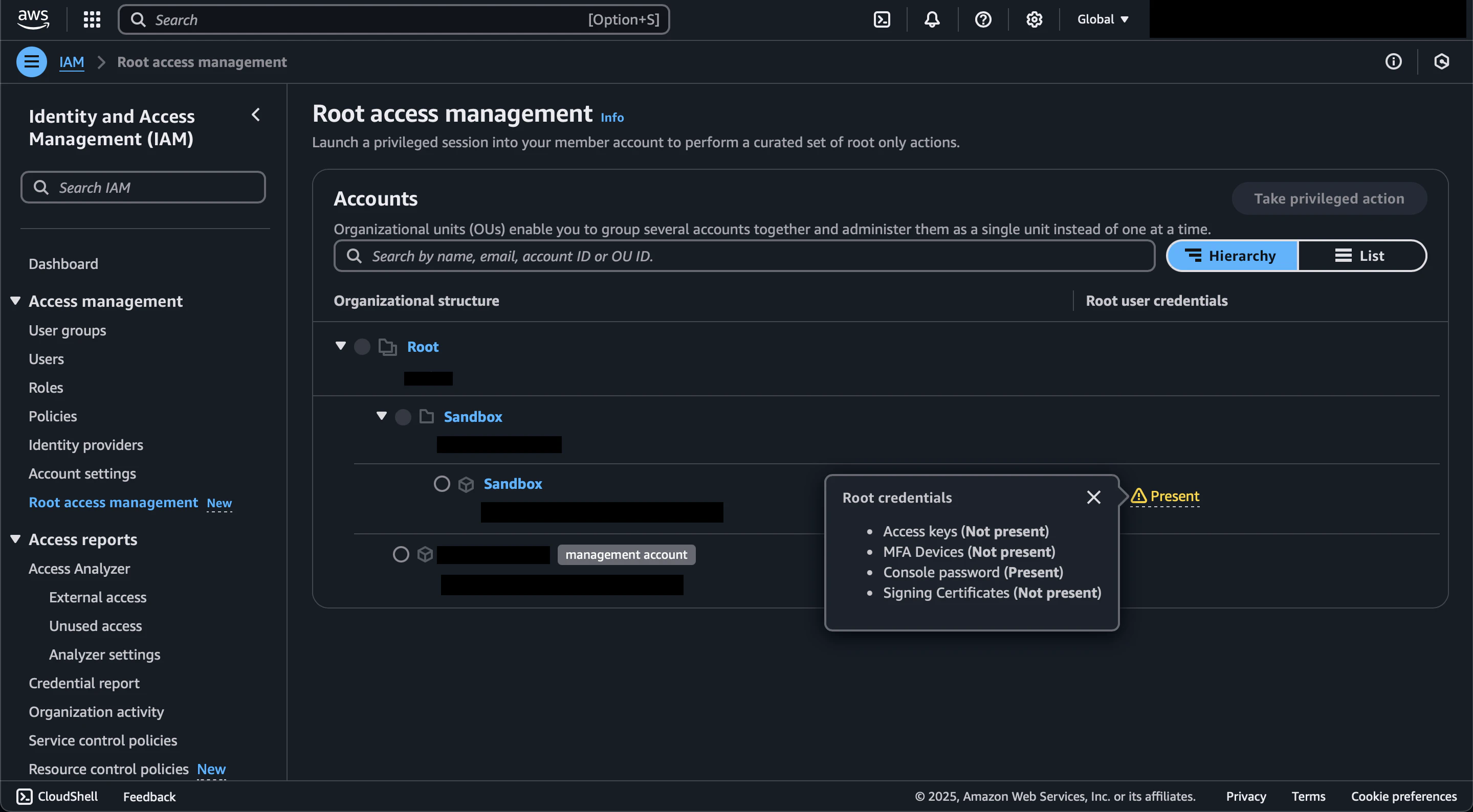
Select the Sandbox account and click the Take privileged action button. In the Privileged action section, select Delete user credentials, review the information, and click the Delete root user credentials button.
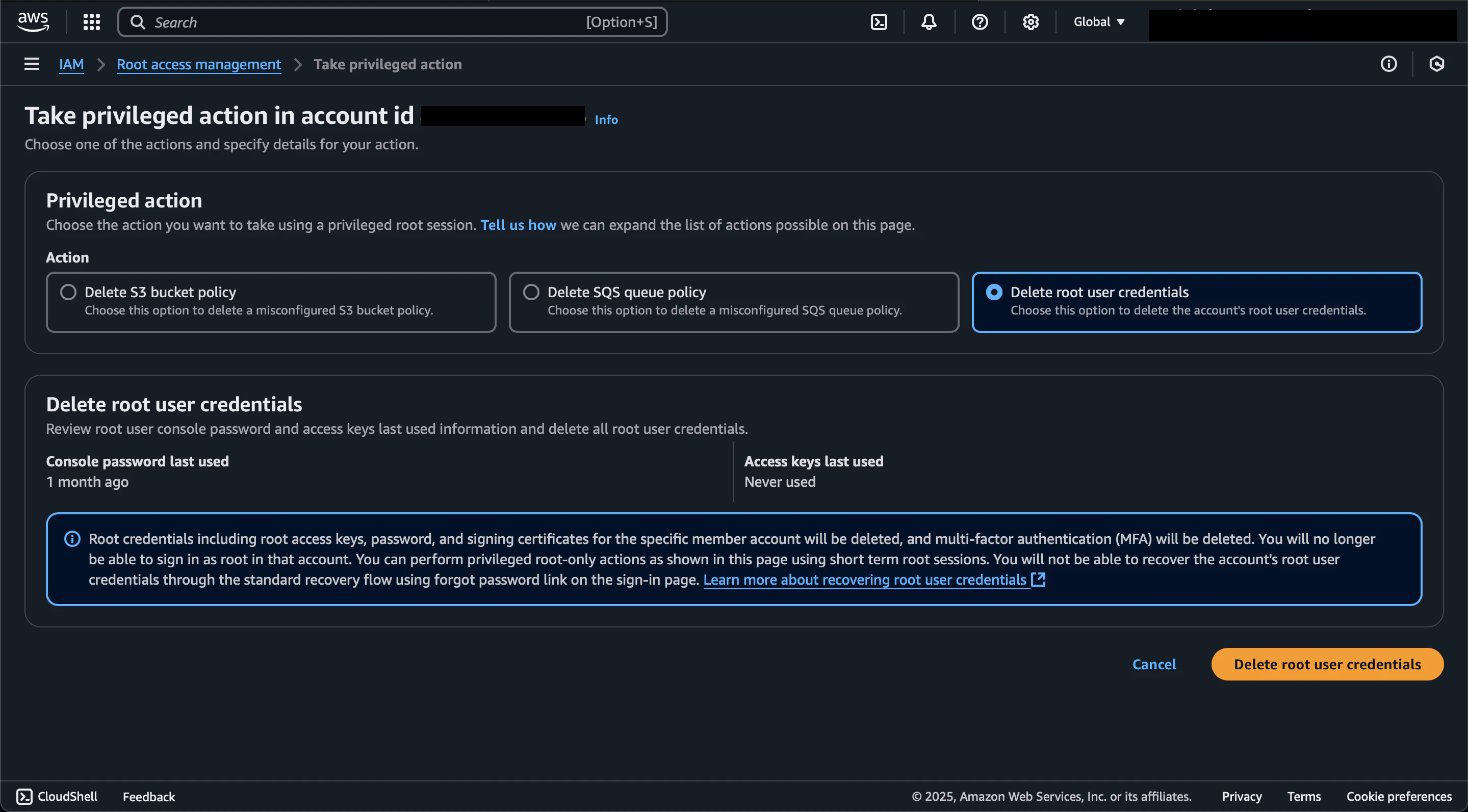
The Sandbox account now shows a status of Not present in the Root user credentials column.
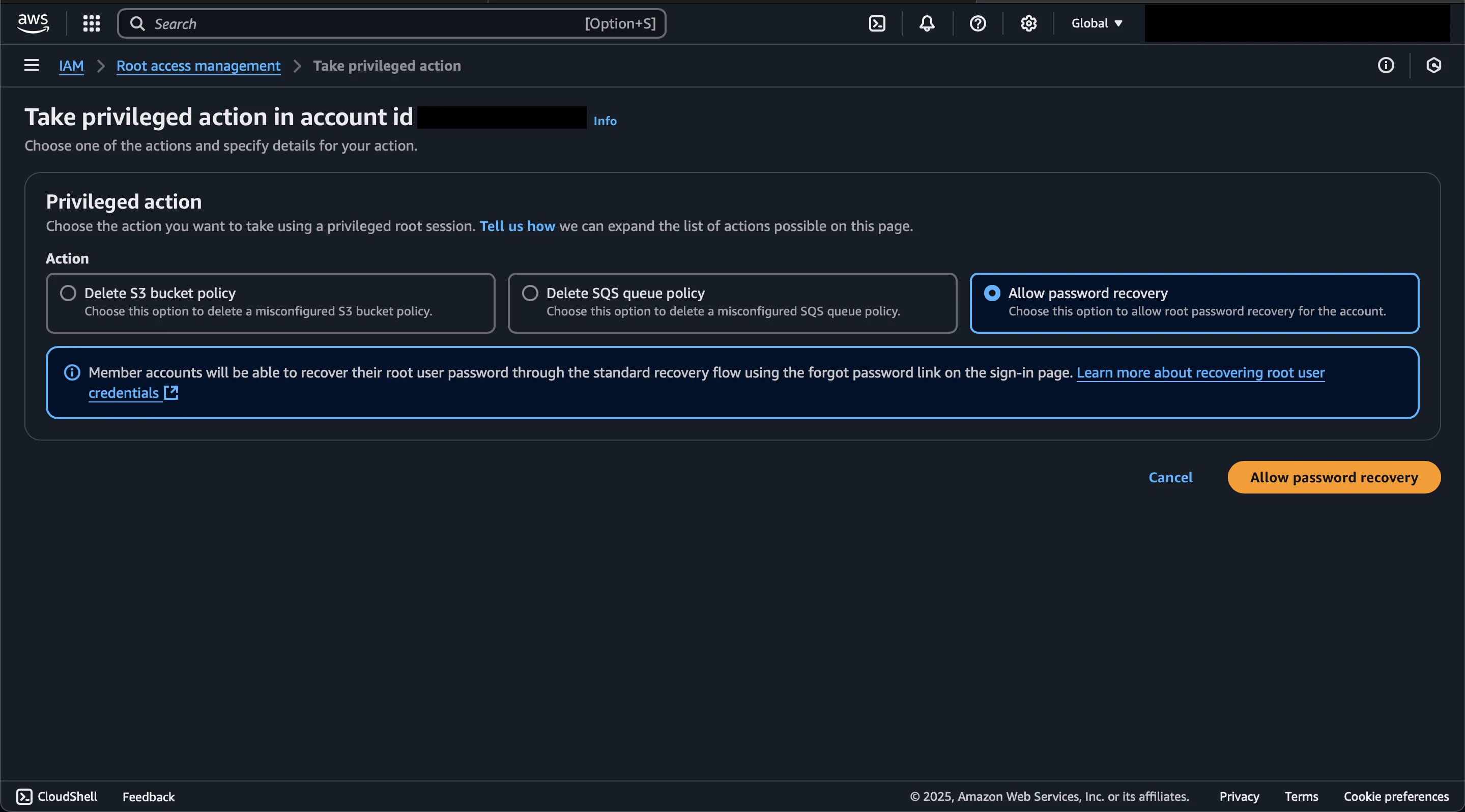
To recover access to the root user, select the Sandbox account again and click the Take privileged action button. In the Privileged action section, select Allow password recovery, review the information, and click the Allow password recovery button.
Manage root credentials or perform privileged actions programmatically#
Root Access Management is a useful tool for managing root credentials in our organization’s accounts, but it doesn’t allow us to manage credentials for multiple accounts at once. This feature would be helpful for large organizations with hundreds of accounts. To solve this, we could create our own automation to interact with the AWS API. Here are some examples of how to use the AWS CLI to:
- Delete root credentials
- Enable root password recovery
Delete root credentials#
The following example illustrates how to delete the root credentials of an AWS member account.
From the Management account, assume the root user in the target account using temporary credentials.
aws sts assume-root --target-principal <Account ID> --task-policy-arn arn=arn:aws:iam::aws:policy/root-task/IAMDeleteRootUserCredentialssts assume-rootcommand scopes the session to the privileged tasks that can be performed based on thetask-policy-arnprovided(1). AWS provides the following managed policies to scope root session actions:- IAMAuditRootUserCredentials
- IAMCreateRootUserPassword
- IAMDeleteRootUserCredentials
- S3UnlockBucketPolicy
- SQSUnlockQueuePolicy
Use the temporary credentials to authenticate as the root user of the target account.
Delete the root credentials.
aws iam delete-login-profile
Enable root password recovery#
The following example shows how to enable the root password in a member account, allowing password recovery.
From the Management account, assume the root user of the target account using temporary credentials.
aws sts assume-root --target-principal <Account ID> --task-policy-arn arn=arn:aws:iam::aws:policy/root-task/IAMCreateRootUserPasswordUse the temporary credentials to authenticate as the root user of the target account.
Enable the root password for the account.
aws iam create-login-profileThe password cannot be set in this step, as AWS generates an unknown random password. From this point, it is possible to recover the root password for the account by following the standard procedure.(2).
Limitations and Caveats#
IAM Root Access Management and Control Tower#
IAM Root Access Management does not work in accounts managed by Control Tower when the control AWS-GR_RESTRICT_ROOT_USER is enabled. This is because the control applies a Service Control Policy (SCP) that prevents any operation from being performed by the root user. Since IAM Root Access Management in the management account assumes the root user in the member account, it is prevented from executing any action required to manage the root user credentials or perform any privileged action.
This is the SCP that the AWS-GR_RESTRICT_ROOT_USER control applies:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "GRRESTRICTROOTUSER",
"Effect": "Deny",
"Action": "*",
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:root"
]
}
}
}
]
}
If, for compliance reasons, you need to keep the root user locked but still want to manage its credentials or perform the allowed privileged actions from the organization’s management account, simply disable the Control Tower control AWS-GR_RESTRICT_ROOT_USER and apply a custom SCP like the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"NotAction": [
"iam:GetAccountSummary",
"iam:DeleteAccessKey",
"iam:DeleteSigningCertificate",
"iam:DeleteLoginProfile",
"iam:DeactivateMFADevice",
"iam:ListAccessKeys",
"iam:ListSigningCertificates",
"iam:GetLoginProfile",
"iam:ListMFADevices",
"iam:GetUser",
"iam:GetAccessKeyLastUsed",
"iam:CreateLoginProfile",
"iam:GetLoginProfile",
"s3:DeleteBucketPolicy",
"s3:PutBucketPolicy",
"s3:GetBucketPolicy",
"s3:ListAllMyBuckets",
"sqs:SetQueueAttributes",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"sqs:GetQueueUrl"
],
"Resource": [
"*"
],
"Condition": {
"ArnLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:root"
]
}
}
}
]
}
Manage root user credentials programmaticaly#
Deleting the root password from a member account using the AWS Console also deletes all of its access keys, X. 509 signing certificates, and disables all multi-factor authentication (MFA) devices.
Programmatically, this must be done explicitly by making the appropriate AWS API calls. For example, a sample algorithm could be:
- Get root temporary credentials using
sts assume-role. - List all root user access keys with
iam list-access-keys. - For each access key, delete it using
iam delete-access-key. - List all root user X.509 signing certificates with
iam list-signing-certificates. - For each X.509 signing certificate, delete it using
iam delete-signing-certificate. - List all root user multi-factor authentication (MFA) devices with
iam list-mfa-devices. - For each MFA device, deactivate it using
iam deactivate-mfa-device.
Wrapping up#
In this post, we explored what IAM Root Access Management is, how to enable it, and how to use it via the AWS Console as well as programmatically.
We also discussed the importance of maintaining a strong security posture regarding root user usage, particularly in AWS Organizations member accounts.
Lastly, we reviewed the tool’s limitations and provided strategies to overcome them.
If you found this article useful, subscribe to the newsletter and get articles, guides, and news about AWS delivered straight to your inbox.
Subscribe

